

Uncover your ideal customers with first-party data
Discover and activate new high-potential customers with advanced lookalikes, powered by your first-party data.
Privacy-minded organizations work with Decentriq
























Better targeting through better quality data
Make reliance on third-party cookies a thing of the past. Use the best available data — your own — to generate audiences with a high likelihood to convert.
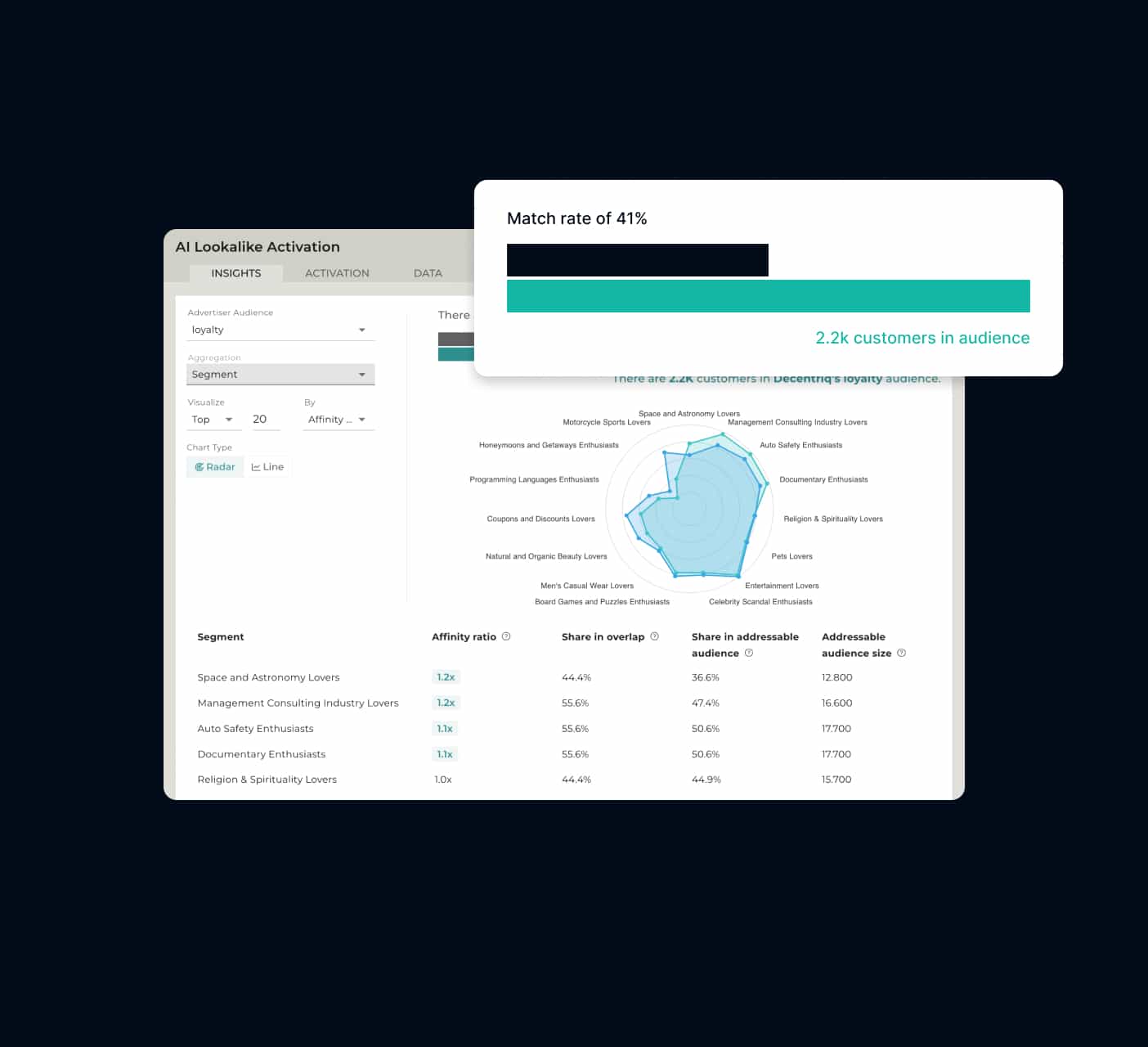
Boost campaign effectiveness beyond walled gardens
129%
Higher click-through rate
27%
Higher page views rate
44%
Lower cost per views
The partnership with Decentriq is an important milestone for us and our customers in a future without third-party cookies in digital marketing. Next to classic media use cases like planning, activation and measurement, we can bring different customers together to collaborate on brand new applications of first-party data — while they retain absolute control over their own datasets.
With limited resources, analyses gets backlogged. Using data clean rooms, we can collaborate and help institutions analyze the data, while they can be fully confident that the data is in their full control, and that no one else - neither Decentriq nor Roche - has access to the raw data itself.
Decentriq enables a whole new perspective on how we can innovate with data that wasn't possible before.
Decentriq's privacy preserving analytics provide a valuable tool in defending supply chains without compromising on sensitive data or trade secrets.
3rd party cookies have underpinned internet advertising for decades. With its deprecation, publishers and brands have to rethink entirely new ways to reach audiences in a privacy-first world. With Decentriq and confidential computing, Goldbach enables a trust layer, allowing brands to onboard their 1st party data without compliance risks.
Learn how data clean rooms are transforming first-party activation
Secure collaboration in the Switzerland of data
Join and analyze data with partners in secure data clean rooms. Backed by advanced privacy technologies like Confidential Computing, your data and your models are never accessible by any other party, not even Decentriq.

Trusted by the world’s most regulated organizations across healthcare, banking, and the public sector
Learn how healthcare organizations are using Decentriq to work across silos. Enabled to securely and compliantly analyze sensitive patient data, they are developing new innovations for diagnostics, treatment and more.

Do more with sensitive data
Secure collaboration could be the key to unlocking value from data you thought was too sensitive to use. Contact us today to learn more or schedule a demo.





